
Pablo Moriano, Ph.D.
Staff Scientist
Computer Science and Mathematics Division
Oak Ridge National Laboratory
moriano [at] ornl.gov
I am a staff scientist in the Computer Science and Mathematics Division at Oak Ridge National Laboratory. I received Ph.D. and M.S. degrees in Informatics from the School of Informatics, Computing, and Engineering at Indiana University Bloomington. Previously, I received M.S. and B.S. degrees in Electrical Engineering at Pontificia Universidad Javeriana in Colombia. I am the recipient of best paper awards at the 9th International Workshop on Managing Insider Security Threats (MIST) 2017 in conjuntion with CCS and the 4th International Workshop on Automative and Autonomous Vehicle Security (AutoSec) 2022 in conjunction with NDSS. In the past, I have done research internships at Cisco Systems, Inc. with the Advanced Security Research Group.
My research lies at the intersection of data science, network science, and cybersecurity.
I use data-driven and computational methods to discover and understand anomalous behavior in large-scale networked systems. I rely on this approach to design and develop innovative solutions to address these. Applications of my research range across multiple disciplines, including, the detection of exceptional events in social media, Internet route hijacking, insider threat behavior in version control systems, and intrusion detection in cyber-physical systems.
Here is a word cloud built out of the abstracts of my papers.

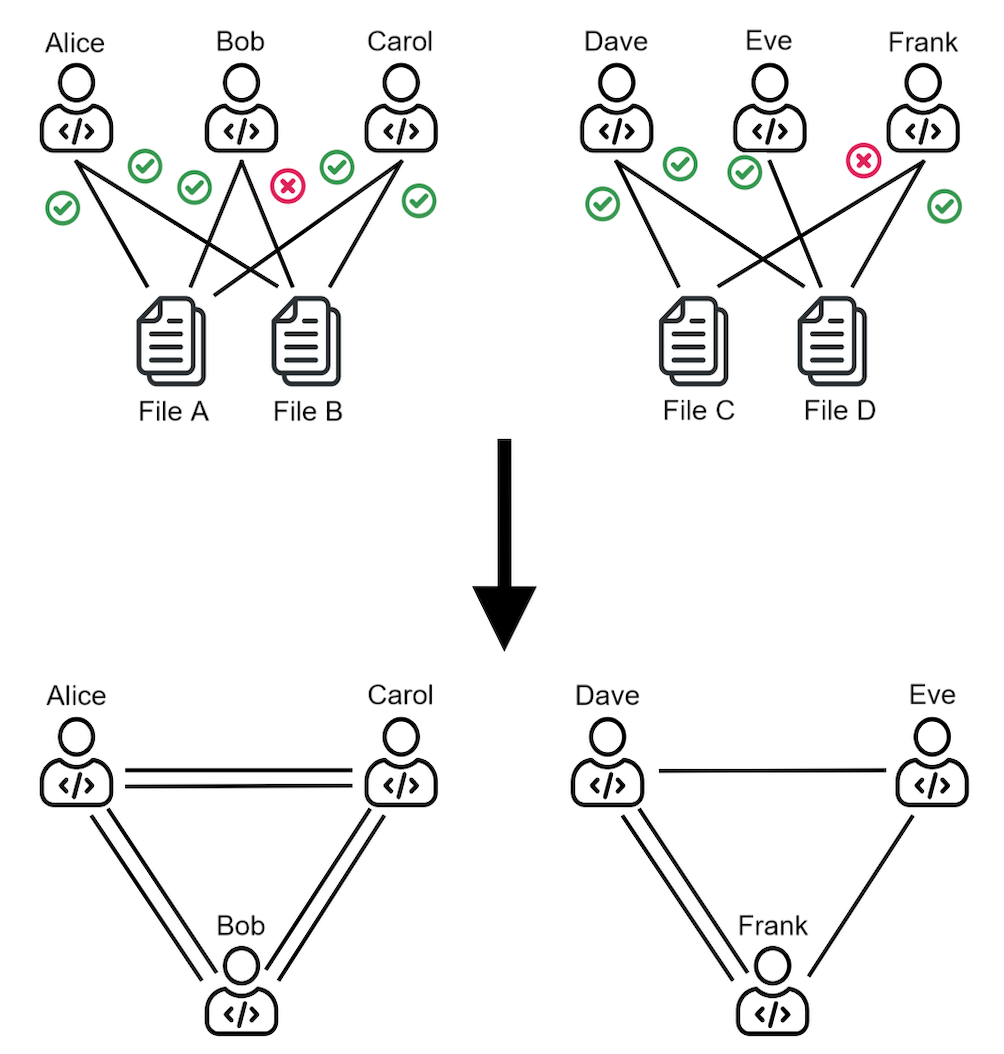
Our research shows the potential of using graph-based ML to improve Just-In-Time (JIT) defect prediction. We hypothesize that features extracted from the contribution graphs may be better predictors of defect-prone changes than intrinsic features derived from software characteristics. We corroborate our hypothesis using graph-based ML for classifying edges that represent defect-prone changes. This new framing of the JIT defect prediction problem leads to remarkably better results.
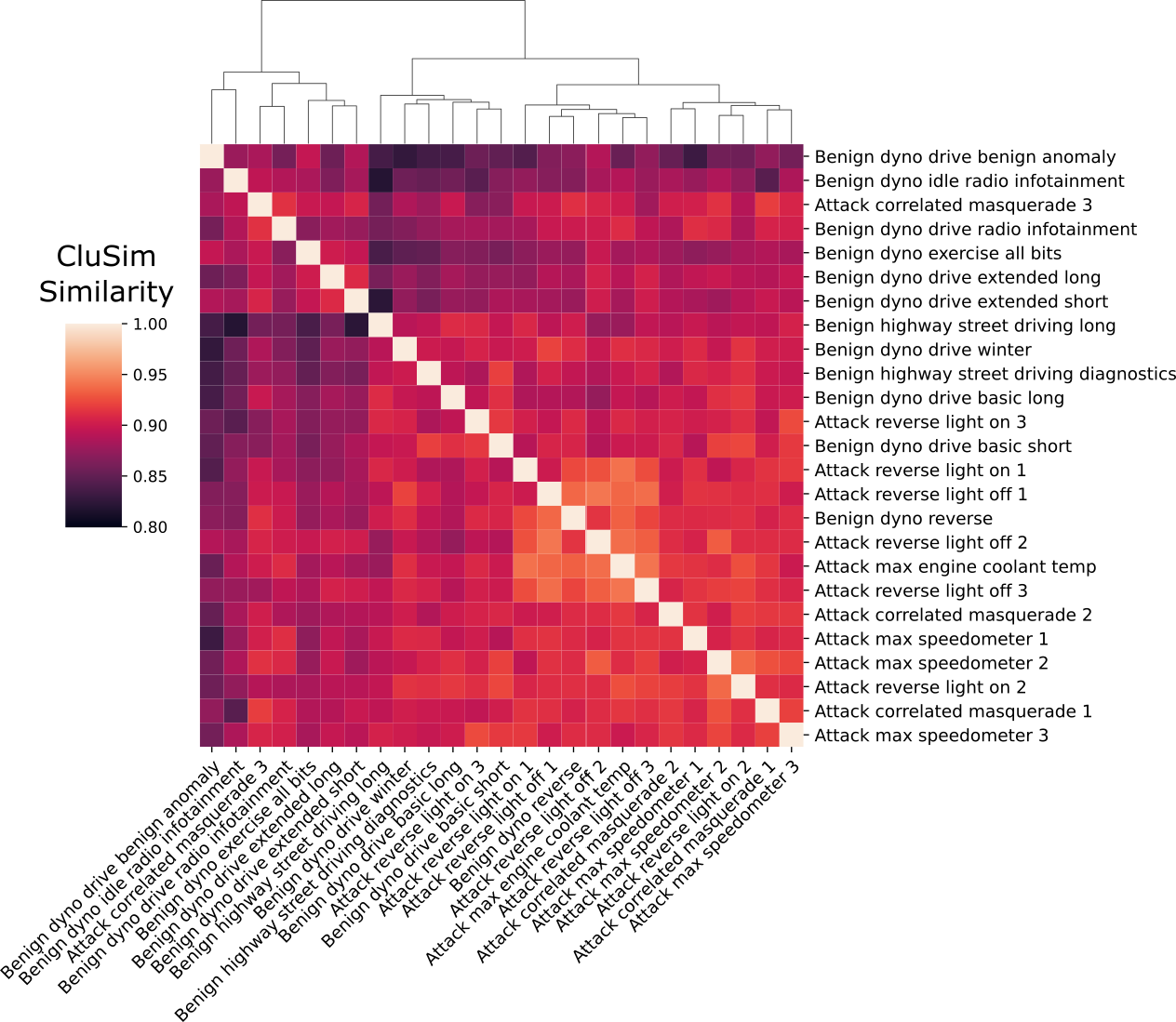
We show that the similarity of time series clusters under benign conditions exhibits statistically significant differences from the similarity of time series clusters under attack conditions. We demonstrated these differences under different attack scenarios with different levels of sophistication using data from the ROAD dataset. This work shows that it is possible to detect masquerade attacks by effectively using the time series clustering representation of signals in the CAN bus and appropriate choices of parameters to group them.
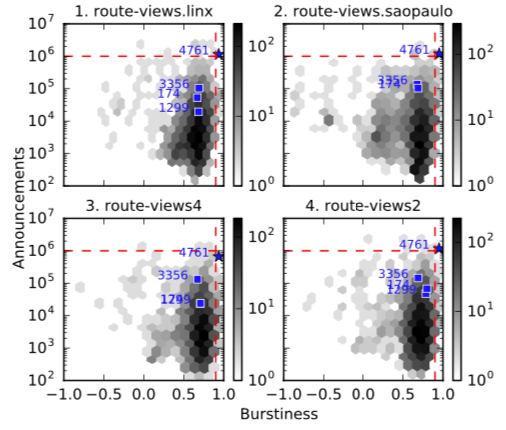
We developed a method for detecting routing anomalies based on the analysis of bursty BGP announcements. I hypothesize that BGP announcements that are associated with disruptive updates tend to occur in groups of relatively high frequency, followed by periods of infrequent activity or high burstiness. I demonstrate the efficacy of this method across different case studies ranging from a hundred thousand to a dozen compromised prefixes.
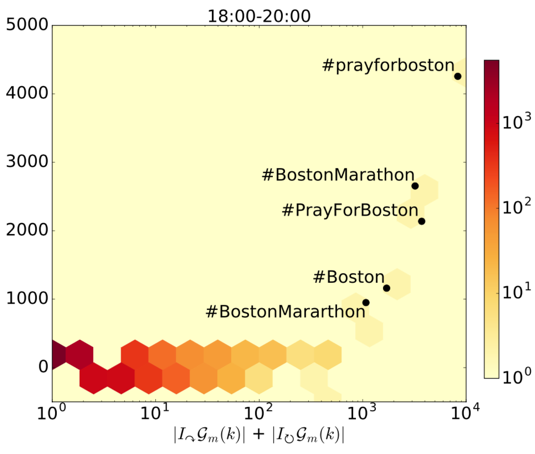
We proposed a method for detecting large events based on the structure of temporal communication networks. I hypothesize that global events trigger viral information cascades that easily cross community boundaries and can thus be detected by monitoring intra- and inter-community communications. By comparing the amount of communications within and across communities, I show that it is possible to detect large-scale events, even when they do not trigger a significantly larger communication volume.

We proposed an unsupervised learning framework to evaluate whether potential insider threat events are triggered following precipitating events. The analysis leverages a bipartite graph of user and system interactions. The approach shows a clear correlation between precipitating events and the number of apparent anomalies. The results of this empirical analysis evidence a clear shift in behaviors after events that previously have shown to increase insider threat incidents.

We analyzed reported routing anomalies and macroeconomic indicators over a four-year period. There are well-documented hijacks resulting from errors, for profit, or for national security and national intelligence purposes. Any individual hijack could be an accident, a crime, or an attack. I report on an empirical investigation into the macroeconomics of routing anomalies that addresses these three explanations.
-
Spatiotemporal features of traffic help reduce automatic accident detection time
Pablo Moriano, Andy Berres, Haowen Xu, and Jibonananda Sanyal
Expert Systems with Applications, June 2024
-
A comprehensive guide to CAN IDS data and introduction of the ROAD dataset
Miki E. Verma, Robert A. Bridges, Michael D. Iannacone, Samuel C. Hollifield, Pablo Moriano, Steven C. Hespeler, Bill Kay, and Frank L. Combs
PLOS ONE, January 2024
-
CANShield: Deep-Learning-Based Intrusion Detection Framework for Controller Area Networks at the Signal Level
Md. Hasan Shahriar, Yang Xiao, Pablo Moriano, Wenjing Lou, and Y. Thomas Hou
IEEE Internet of Things Journal, December 2023
-
Robustness of community structure under edge addition
Moyi Tian and Pablo Moriano
Physical Review E, November 2023
-
Graph-based machine learning improves just-in-time defect prediction
Jonathan Bryan and Pablo Moriano
PLOS ONE, April 2023
-
Detecting CAN Masquerade Attacks with Signal Clustering Similarity
Pablo Moriano, Robert A. Bridges, and Michael D. Iannacone
AutoSec, April 2022 Best paper award
-
Using bursty announcements for detecting BGP routing anomalies
Pablo Moriano, Raquel Hill, and L. Jean Camp
Computer Networks, January 2021
-
Anomaly Detection in Real-World Temporal Networks
Pablo Moriano
PhD Dissertation. Indiana University, May 2019
-
Community-Based Event Detection in Temporal Networks
Pablo Moriano, Jorge Finke, and Yong-Yeol Ahn
Scientific Reports, March 2019
-
Insider Threat Event Detection in User-System Interactions
Pablo Moriano, Jared Pendleton, Steven Rich, and L. Jean Camp
MIST, October 2017. Best paper award
-
Incompetents, Criminals, or Spies: Macroeconomic Analysis of Routing Anomalies
Pablo Moriano, Soumya Achar, and L. Jean Camp
Computers & Security, September 2017
-
On the Formation of Structure in Growing Networks
Pablo Moriano and Jorge Finke
JSTAT, June 2013
-
Power-Law Weighted Networks from Local Attachments
Pablo Moriano and Jorge Finke
EPL, July 2012
Please email me if you are applying for an internship to work with me directly. There are five main programs: SULI (undergrad, STEM fields), NSF MSGI (graduate, math-related fields), OMNI (graduate, CS-related fields), GEM (graduate, STEM fields), and SCGSR (graduate, STEM fields).
Note: Deadlines vary and some require coordination with an ORNL sponsor. Therefore, contact me well in advance if you are interested.
Postdoc
- Steven C. Hespeler, Laboratory Directed Research and Development (LDRD) Program, 2023. From New Mexico State University
Graduate
- Dalya Manatoba, Graduate Research at ORNL (GRO) Program, 2025. From Indiana University
- Nehal Ameen, DOE Omni Technology Alliance Internship Program, 2024. From Virginia Commonwealth University
- Jaidev Goel, Graduate Research at ORNL (GRO) Program, 2024. From Virginia Tech
- William Marfo, Sustainable Research Pathways (SRP) Program, 2023. From The University of Texas at El Paso
- Zhifeng Wei, NSF MSGI Fellow, 2023. From Indiana University. Postdoctoral Fellow, Pacific Northwest National Laboratory
- Moyi Tian, NSF MSGI Fellow, 2022. From Brown University. Postdoctoral Fellow, University of Colorado Boulder
Undergraduate
- Jonathan Bryan, DOE SULI Fellow, 2021. From University of Tennessee, Knoxville. Software Engineer at Microsoft
Journal Referee
- Journal of Traffic and Transportation Engineering
- IEEE Transactions on Industrial Informatics
- ACM Transactions on Software Engineering and Methodology
- IEEE Network
- IEEE Transactions on Cybernetics
- Expert Systems with Applications
- IEEE Transactions on Dependable and Secure Computing
- IEEE Transactions on Intelligent Transportation Systems
- Ad Hoc Networks
- IEEE Transactions on Information Forensics and Security
- IEEE Transactions on Network Science and Engineering
- Social Networks Analysis and Mining
- Journal of Information Security and Applications
- Intelligent Systems with Applications
- Computer Networks
- Chaos
- Computers & Security
- PLOS One
- IEEE Transactions on Knowledge and Data Engineering
- IEEE Access
- ACM Transactions on Information and System Security (TISSEC)
Technical Program Committees
- 17th ACM Workshop on Artificial Intelligence and Security, 2024
- The International Conference for High Performance Computing, Networking,Storage, and Analysis (SC), 2021
- ACM Internet Measurement Conference (Shadow PC), 2017
- IFAC Conference on Technology, Culture and International Stability
One Bethel Valley Road
PO Box 2008, MS6013
Oak Ridge, TN 37831, USA
(865) 341-2768
 PDF
PDF  BibTeX
BibTeX